SSH Port Forwarding is a widely used technique that lets you securely reach services running on remote or private networks. Developers, sysadmins, and DevOps teams use it to access internal web apps, databases, admin panels, and APIs without exposing them directly to the public internet.
In simple terms, SSH Port Forwarding creates an encrypted tunnel between your computer and a server. Traffic sent through that tunnel is forwarded to a destination port, safely. It’s powerful, but it can also get tricky fast—especially when you’re juggling multiple ports, reconnects, firewall rules, or sharing access with teammates.
This guide explains what SSH Port Forwarding is, how it works, the main types (local/remote/dynamic), and common real-life use cases. Then we’ll show an easier approach: you can do the same thing much more simply using Localtonet’s Zero-Install SSH tunneling.
What Is SSH Port Forwarding?
SSH Port Forwarding (also called SSH tunneling) is a method of routing network traffic through an SSH connection. Because SSH encrypts the connection, the forwarded traffic is protected from eavesdropping and tampering.
It’s commonly used to:
- Access internal services behind a firewall
- Secure traffic for services that aren’t encrypted by default
- Expose a local development server temporarily
- Reach remote resources safely from untrusted networks
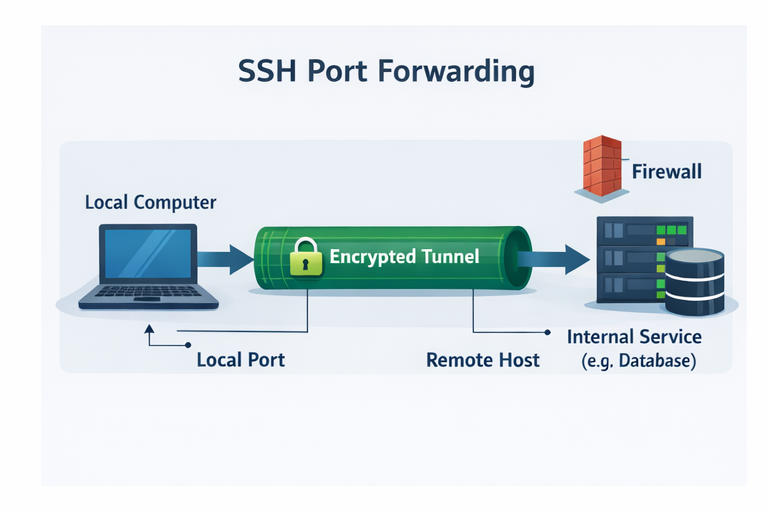
How SSH Port Forwarding Works
Think of SSH Port Forwarding like a secure “pipe” you create using SSH:
- You open an SSH connection to a remote server you can reach.
- You bind a local (or remote) port to that SSH connection.
- When something connects to that port, SSH sends the traffic through the encrypted tunnel.
- The remote side forwards it to the destination service (like a database or web server).
That’s the idea. In practice, you may need to handle key authentication, user permissions, firewall settings, and tunnel stability. If the SSH session drops, the tunnel drops too—meaning you often need to reconnect or run keep-alive settings.
Types of SSH Port Forwarding
1) Local Port Forwarding
Local forwarding forwards a port from your local machine to a destination reachable from the remote SSH server. This is perfect when the service is inside the remote network.
Typical use: You want to access a private database running on a server network.
ssh -L 8080:localhost:80 user@remote-serverNow, when you open http://localhost:8080, your traffic is securely forwarded to localhost:80 from the perspective of remote-server.
2) Remote Port Forwarding
Remote forwarding exposes a local service (on your computer) to the remote server. This can be useful when you need someone to access your local dev app via the remote server.
Typical use: Share a local web app temporarily.
ssh -R 9000:localhost:3000 user@remote-serverWith this, requests to port 9000 on the remote server get forwarded to localhost:3000 on your machine.
3) Dynamic Port Forwarding
Dynamic forwarding turns SSH into a SOCKS proxy. Instead of forwarding one specific port to one destination, you can route many connections through a proxy.
Typical use: Secure browsing or accessing multiple internal endpoints.
ssh -D 1080 user@remote-serverYou then configure your browser or OS to use SOCKS proxy localhost:1080.

Common Use Cases for SSH Port Forwarding
- Secure database access: Connect to PostgreSQL/MySQL in a private subnet.
- Internal admin panels: Reach internal dashboards without exposing them publicly.
- API testing: Test services running on staging environments behind firewalls.
- Temporary exposure: Share a local service (remote forwarding) for a short time.
- Encrypted transport: Protect traffic that isn’t encrypted by default.
Limitations and Challenges of SSH Port Forwarding
SSH Port Forwarding is reliable and secure, but it can be a headache in day-to-day workflows:
- Complex commands: Easy to make mistakes in syntax and port mapping.
- Manual setup: Each service/port usually needs its own configuration.
- No instant public URL: Sharing often requires extra infrastructure.
- Connection drops: When SSH disconnects, your tunnel goes down.
- Not beginner-friendly: Requires comfort with networking and CLI.
A Much Easier Alternative: You Can Do This with Localtonet
Here’s the practical reality: you can absolutely do SSH Port Forwarding the classic way—but you can also achieve the same end result far more easily using Localtonet.
Localtonet provides secure tunneling that helps you expose local services to the internet without manually managing SSH port forwarding rules, firewall settings, or repeated command tweaking. If your goal is “make my local app accessible securely,” a modern tunneling workflow can save time and reduce errors.
Official documentation (Zero-Install SSH): https://localtonet.com/documents/zero-install-ssh
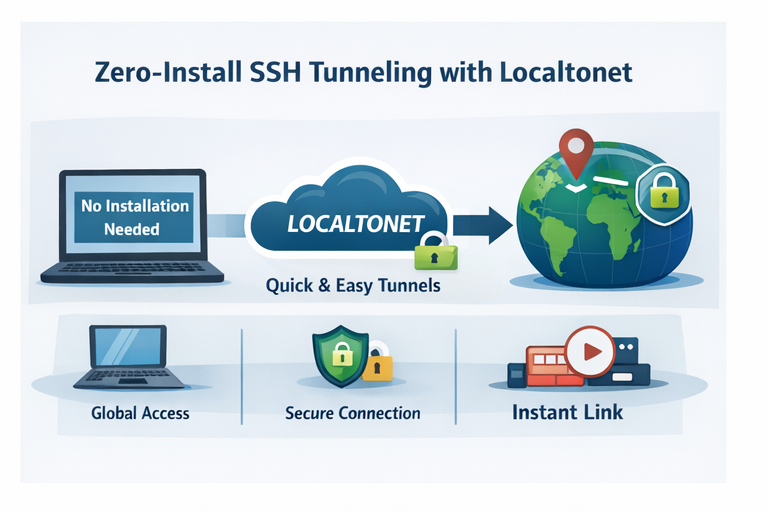
Zero-Install SSH Tunneling with Localtonet
One feature that stands out is Localtonet’s Zero-Install SSH approach. The promise is straightforward: less setup, fewer moving parts, and faster results.
Instead of spending time on SSH flags and port-forwarding configurations, you can typically:
- Run your local service (example:
localhost:3000) - Use the Localtonet SSH method from their documentation
- Get a public URL that routes to your local service securely
This can be especially useful when you need to share demos, test webhook callbacks, or let teammates view a local environment without asking them to set up VPNs or SSH tunnels.
SSH Port Forwarding vs Localtonet
| Feature | SSH Port Forwarding | Localtonet |
|---|---|---|
| Setup time | Medium to high | Low |
| Command complexity | Higher (flags, ports, mapping) | Lower (simplified workflow) |
| Public URL | Not automatic | Typically provided |
| Stability | Depends on SSH session | Often managed by service |
| Beginner-friendly | Not really | More friendly |
Frequently Asked Questions (FAQs)
1) Is SSH Port Forwarding secure?
Yes. SSH encrypts traffic end-to-end through the tunnel. Security depends on proper key management, server hardening, and access controls.
2) What’s the difference between local and remote port forwarding?
Local forwarding exposes a remote/internal resource to your local machine. Remote forwarding exposes your local resource to the remote server side.
3) Why does my SSH tunnel disconnect?
Tunnels can drop due to network instability, timeouts, sleep mode, server settings, or idle session rules. Keep-alive settings and stable networks help.
4) Do I need to open firewall ports for SSH Port Forwarding?
Usually you only need SSH access (commonly port 22) to the remote server. But the destination service must be reachable from the remote server’s network.
5) Can Localtonet replace SSH Port Forwarding?
For many workflows—like sharing local web apps, testing webhooks, and exposing dev servers—yes, it can be a simpler alternative.
6) Where can I learn Localtonet’s Zero-Install SSH method?
Use the official documentation here: https://localtonet.com/documents/zero-install-ssh
Conclusion
SSH Port Forwarding is a classic, powerful tool for secure tunneling and accessing private services. But it can be fiddly: commands are easy to mess up, tunnels can drop, and sharing access isn’t always straightforward.
If your goal is simply “securely expose my local service,” you can still use SSH Port Forwarding—but you can also do it much more easily with Localtonet, especially using their Zero-Install SSH approach. That way you spend less time configuring tunnels and more time building.


